[BUUCTF]findit
是个apk, 拿AndroidKiller反编译,
找到一个Unicode字符串
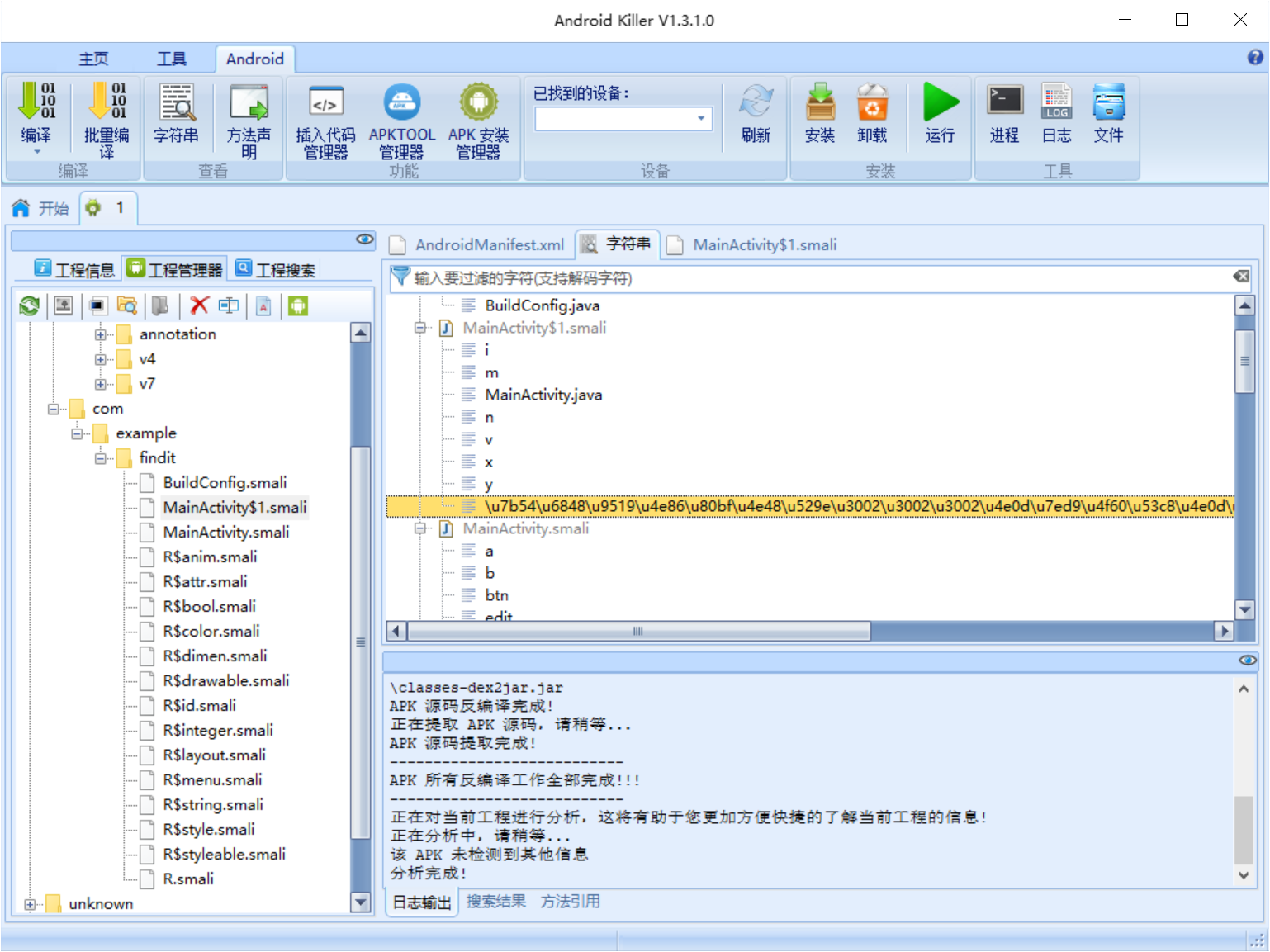
解码一看, 哈哈高兴的太早了
1 | string = "\u7b54\u6848\u9519\u4e86\u80bf\u4e48\u529e\u3002\u3002\u3002\ |
在MainActivity.smali里面找到了几个数组,
很可能和flag有关
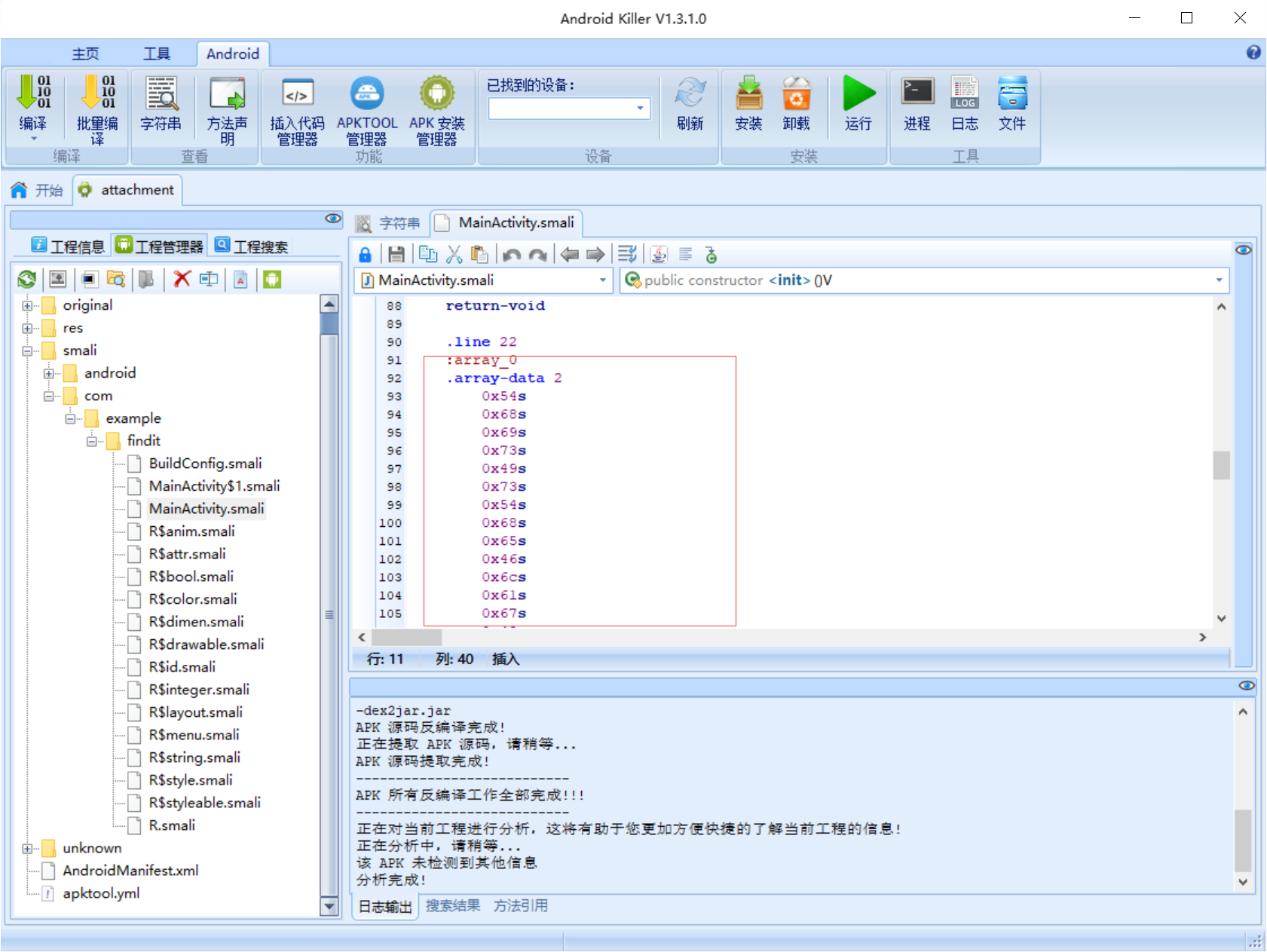
smali格式阅读起来很不方便,
需要将它还原成Java代码,
但是AndroidKiller不支持这种功能,
所以改用jadx.
jadx: Github
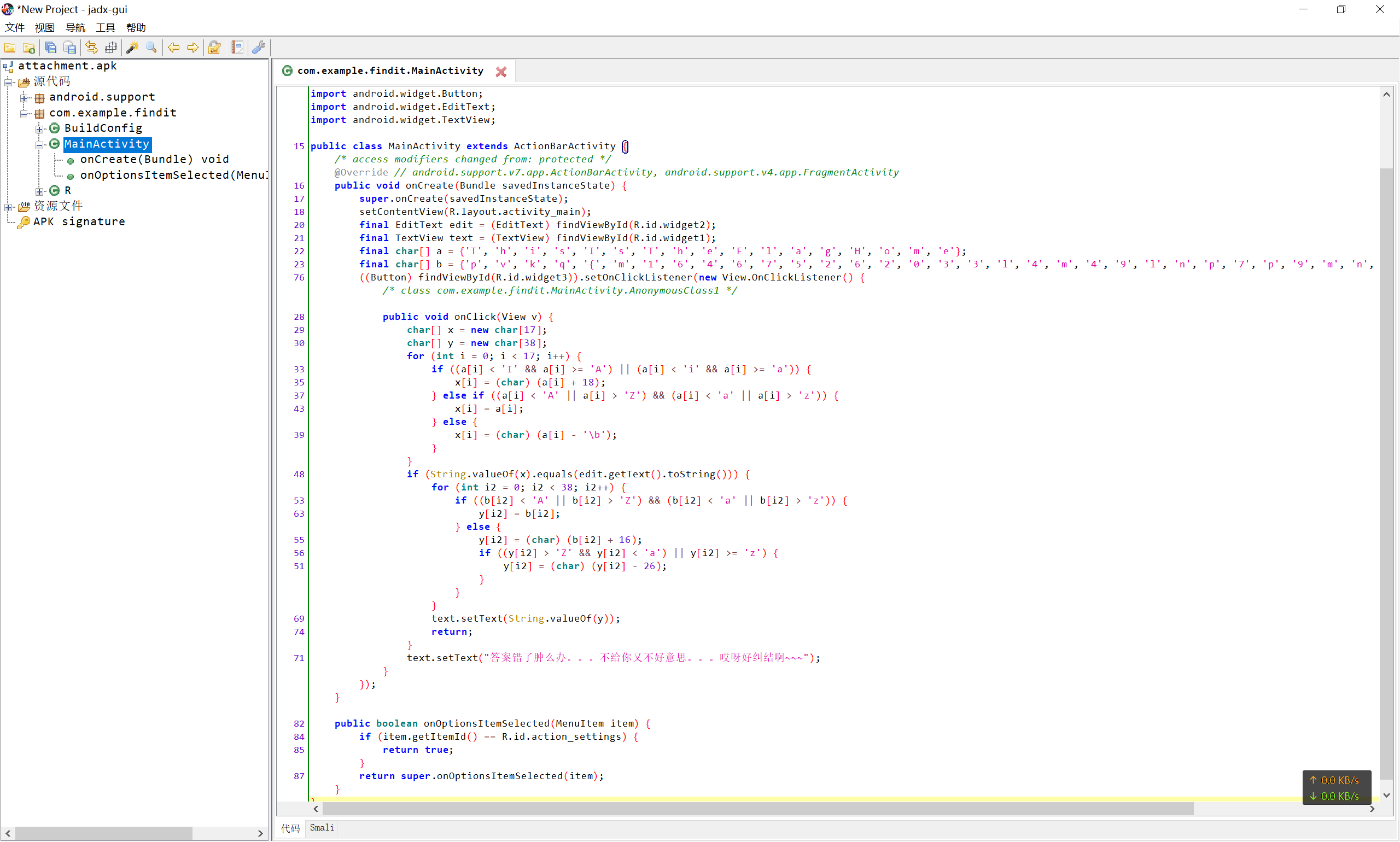
用jadx-gui直接打开apk, 源码就出来了,
到MainActivity一看, 果然和flag有关
1 | package com.example.findit; |
好在Java的语法和C/C++类似,
可以大概看出来是个啥意思:
先对a数组进行处理, 放到x数组中,
对比用户的输入和x数组是否相同,
若相同则对b数组进行处理放到y数组中并显示出来,
想必y数组中的就是flag.
解密代码如下:
1 |
|